Penetration Testing Services
Securing Your Digital Infrastructure Against Emerging Threats with our Penetration Testing Services
Comprehensive Pentesting
Thorough and meticulous Penetration testing conducted by premier Ethical hackers, securely accessible via an advanced online portal.
Uncover and address vulnerabilities in compliance with industry standards, simplifying audits.
Get a Pentest Quote
Penetration Testing as a Service (PTaaS)
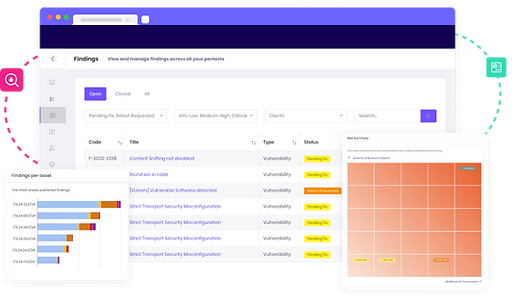
PTaaS Features
- 01/ Intuitive Cloud Dashboard
- 02/ Compliance Ready
- 03/ Team Collaboration
- 04/ Automated Workflows
- 05/ CyberSecurity Services Expertise
PTaaS Benefits
Agile Integration
Continuous Security
Access To Experts
BUZZ Penetration Testing Services
Explore our extensive Pen Testing Services – Web, API, Mobile, Thick Client, and Networks.
Our expert team delivers in-depth evaluations, all accessible through our Pentest-as-a-Service portal.

Web Penetration Testing
- Specialized in Multiple Web Frameworks
- Adherence to Top Security Standards
- Tailored Vulnerability Analysis
- Real-World Attack Simulation

API Pentesting
- Comprehensive API Coverage
- Automated & Manual API Testing
- Security Protocol API Assessment
- API Abuse Case Analysis

Network Pentesting
- Coverage of Internal & External Networks
- Firewall & IDS testing
- Advanced Attacks – DDoS, DNS, and More
- Includes Cloud Penetration Testing

Mobile Application Penetration Testing
- Mobile Specific Tailored Testing
- Coverage Across App Communications
- Traffic Interception Testing
- Advanced Testing for Secure Connections

Thick Client Pentesting
- Local Environment Testing
- Check Client-Server Interactions
- Assess Installation and Runtime Settings
- Identify Potential Backdoors and Breaches
Tailored Pentesting
It’s Time to BUZZ!
We’ll secure
your digital world.
Our Penetration Testing Methodology

1. Discover
- Initial risk assessment and scope definition.
- Gathering intelligence on target systems.
- Customizing testing strategies to fit your environment.

2. Attack
- Attempting controlled breaches to assess risk by Ethical hackers
- Exploiting vulnerabilities in a safe environment.
- Documenting successful exploits for remediation.

3. Report
- Detailed reporting on findings and implications.
- Prioritized remediation strategies.
- Constructive feedback for long-term security enhancement.

4. Remediate & Retest
- Verifying the implementation of security fixes.
- Retesting to confirm closure of vulnerabilities.
- Continuous support for ongoing security improvement.
NOT SURE WHAT TO CHOOSE ?
Why Choose BUZZ for PCI-DSS Compliance Services?
Pentesting Expertise
- 01/ Personalized and tailored testing strategies
- 02/ Deep knowledge of the latest cyber threat landscape
- 03/ Cloud Based Pentest-as-a-Service platform

Globally Certified Team
- 01/ Diverse Certifications - OSCP, OSWE, CEH, Ethical Hackers
- 02/ Red Team Expertise - Synack Red Teams and CRTO
- 03/ Experienced Cybersecurity Specialists
Trusted by companies of all sizes





Why is Pentesting important for an organization?
Identify Vulnerabilities by uncovering and addressing security weaknesses before they become exploitable.
Compliance Assurance is achieved by meeting regulatory requirements. Ex. PCI DSS Compliance, ISO Compliance, GDPR compliance, SOC-2 Compliance, HIPPA Compliance
Enhance Security Posture by strengthening defenses against evolving cyber threats.
Protect Customer Trust through safeguarding sensitive customer data and maintaining your reputation.
Avoid Financial Losses by preventing costly breaches and downtime associated with cyber attacks.
Stay Ahead of Attackers by understanding and mitigating potential attack vectors proactively.
Industries We Serve

Health-Tech

Fin-Tech

Ed-Tech

Retail-Tech
Request a Penetration Test
Frequently Asked Questions - FAQs
Credits earned by the Founder & BUZZ
OTHER SECURITY ASSESSMENTS SERVICES

Risk Assessment

Vulnerability Assessment
Resources
- All Posts
- BUZZ Essentials
- Compliance Simplified
- How-To




