
Security Assessments
Comprehensive Security Analysis Tailored To Your Needs.
Customized & Flexible Security Assessments
We help fast growing companies improve their security posture with a wide range of expert security assessments that are transparent and flexible.
Our efficient PtaaS platform delivers real-time insights, swift results, high collaboration, thorough evaluation of your web, mobile, API, network, and cloud assets - providing full coverage while staying flexible.
CORE SECURITY ASSESSMENTS
Vulnerability Assessment
Conduct comprehensive vulnerability scans across internal, external, and cloud environments. Benefit from our continuous vulnerability management that ensures you're always a step ahead. With us, you get clarity over clutter; our reports filter out the noise, delivering only clear, actionable insights.


Penetration Testing
Experience authentic cyber attack simulations to uncover potential threats, backed by our team's diverse expertise spanning Web, Mobile, APIs, and IoT. Our Pentest-as-a-Service offers a collaborative dashboard for real-time insights. Receive detailed reports with clear mitigation strategies, and count on our continuous support beyond the assessment.
Risk Assessment
Utilizing the NIST framework, we offer a meticulous threat assessment aligned with top industry standards. Our approach prioritizes risks, to tackle the most pressing vulnerabilities first. Benefit from our 5-Point Maturity Model for clear security enhancement steps, executive-friendly reports emphasizing key risks, and our commitment to secure your future, beyond identifying its challenges.

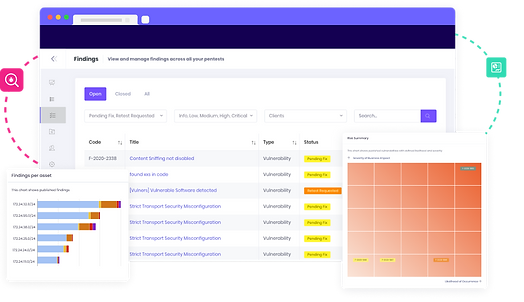
Pentest-as-a-Service (PtaaS) Platform
Integrate pentests effortlessly with our cloud-based PtaaS platform. It offers an all-in-one dashboard for projects, findings, and reports, eliminating email clutter and streamlining processes. Stay compliant with our rigorous, industry-standard pentests conducted by top experts. Receive detailed reports with actionable insights, metrics, and compliance mapping.
Trusted by companies of all sizes

Credits earned by the Founder & BUZZ
Mahendra Pratap
CEO, Asti Solutions
"BUZZ swiftly identified key vulnerabilities in our security, implementing access control and architectural changes.Their hands-on approach made them an extension of our team, not just a vendor, enhancing our overall success."
Manish Talwar
CEO, Goalstox
"Our partnership with BUZZ for a penetration test was impressive. Their speed, thoroughness, and professionalism identified critical vulnerabilities, making them a top recommendation for comprehensive security assessments."
Anirban Mukherji
CEO, miniOrange
"As miniOrange's technical co-founder, Sushma crafted a scalable, secure, and sustainable technical architecture for the initial IDP product, often burning the midnight oil. Her hands-on demos, even under tight timelines, consistently delighted our customers."


