CYBER PROTECT
Cyber Protection As a Service
Securing Your Business in a Digital Age
At BUZZ, we’re not just about defense; we’re about enabling your business to thrive without the looming shadow of cyber threats. Our Cyber Protection as a Service (CPaaS) is meticulously crafted to bolster your organization’s digital defenses. With us by your side, you can focus on scaling your business, knowing that your data, systems, and access points are fortified and resilient.
CORE OFFERINGS

Secure Architecture
Building a secure architecture ensures that your organization stands strong, not just against today’s threats but also prepares it for future challenges.

Data Protection
Protecting your data is more than just a security measure; it’s about ensuring the trust and confidence of your stakeholders.

Incident Response
A swift and effective incident response can mean the difference between a minor hiccup and a major catastrophe.

Access Management
Effective access management is pivotal in safeguarding your systems and data from unauthorized access.

Secure Architecture
Building a secure architecture ensures that your organization stands strong, not just against today’s threats but also prepares it for future challenges. At BUZZ, our Security Architecture Review delves deep into your setup, pinpointing potential vulnerabilities. We then offer pragmatic solutions that not only strengthen your defenses but also meet your business objectives.
What We Do
- Secure Coding: Adopting best practices to craft code that’s both efficient and free from vulnerabilities.
- Architecture Review: A deep dive into your digital infrastructure to ensure all components are integrated securely.
- Supply Chain Reviews: A thorough examination of your supply chain, identifying and mitigating any lurking security risks.
- Threat Modeling: A proactive approach to understanding potential threats, gauging exposure points, and prioritizing them for comprehensive protection.
- Deployment Review: Ensuring that every deployment is optimized for security, leaving no stone unturned in our quest to shield your assets.
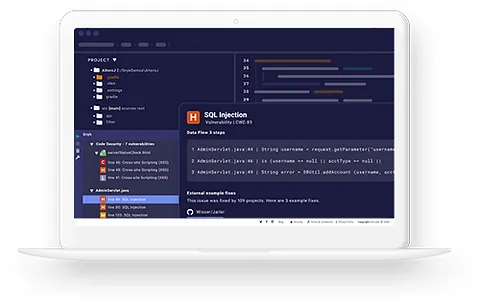

Data Protection
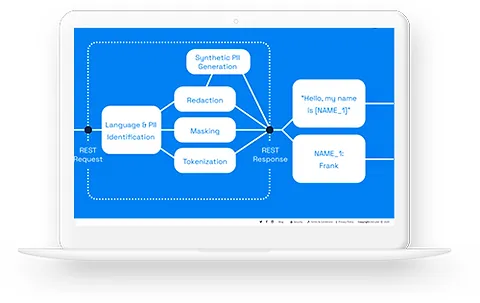
Protecting your data is more than just a security measure; it’s about ensuring the trust and confidence of your stakeholders. At BUZZ, we understand the value of your data and the implications of any breach. Our Data Protection services are designed to safeguard your most valuable asset, ensuring it remains confidential, integral, and available at all times.
What We Do
- Data Classification: We categorize your data based on its sensitivity, ensuring that the right protection measures are applied to the right data sets.
- Encryption & Tokenization: Implementing strong encryption methods and tokenization so your data remains unreadable and secure, even if accessed without authorization.
- Access Control: Setting up strict access controls to ensure only authorized personnel can access sensitive data.
- Data Backup & Recovery: Regularly backing up your data and having a robust recovery plan in place to ensure business continuity in the event of any unforeseen incidents.
- Data Lifecycle Management: Overseeing the entire lifecycle of your data, from creation to disposal, so it remains protected at every stage.

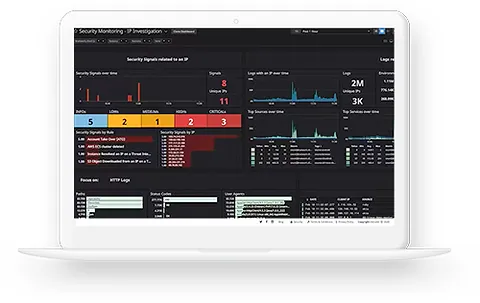
Incident Response
A swift and effective incident response can mean the difference between a minor hiccup and a major catastrophe. At BUZZ, we don’t just monitor; we prime your organization for swift and effective response to potential cyber incidents. Our approach ensures that when a threat emerges, you’re not just reacting — you’re two steps ahead.
What We Do
- Readiness Establishment: We lay the groundwork, ensuring your organization is well-prepared and equipped to handle potential cyber incidents.
- System Monitoring & Breach Assessment: While we don’t actively monitor customer systems, we set up robust mechanisms that allow you to monitor your systems effectively and assess any security breaches promptly.
- Threat Isolation: In the face of a threat, we guide you on how to quickly isolate it, preventing further spread and potential damage.
- Rapid System Restoration: Leveraging our expertise, we assist in restoring affected systems swiftly, minimizing downtime and business impact.
- Continuous Improvement: Post-incident, we help refine and enhance your response strategies, so you’re better prepared for future threats.

Access Management
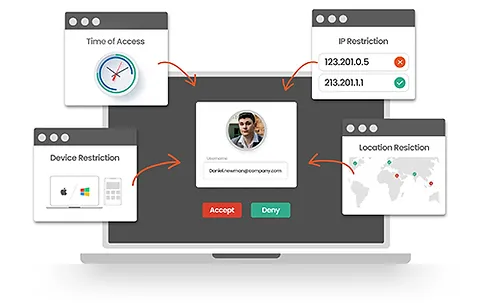
Effective access management is pivotal in safeguarding your systems and data from unauthorized access. It creates a seamless flow where only the right individuals have the keys to specific parts of your organization’s network, applications, and data. At BUZZ, we specialize in crafting such intricate yet user-friendly access systems.
What We Do
- Identity Verification: Implementing robust mechanisms to ensure that users are who they claim to be.
- Role-Based Access Control: Structuring access based on roles, ensuring individuals only access resources relevant to their job functions.
- Single Sign-On (SSO) Implementation: Streamlining access by allowing users to tap into multiple applications with one set of credentials.
- Multi-Factor Authentication (MFA): Enhancing security by requiring multiple verification methods, adding depth to the access control.
- Access Reviews & Audits: Regularly evaluating and refining access rights to stay in sync with organizational needs and security standards.
Trusted by companies of all sizes





Please leave your details.
We’ll BUZZ you!
THAT’S NOT ALL
Learn more about other Services
Credits earned by the Founder & BUZZ
"BUZZ swiftly identified key vulnerabilities in our security, implementing access control and architectural changes.Their hands-on approach made them an extension of our team, not just a vendor, enhancing our overall success."
Mahendra Pratap
CEO, Asti Solutions
"Our partnership with BUZZ for a penetration test was impressive. Their speed, thoroughness, and professionalism identified critical vulnerabilities, making them a top recommendation for comprehensive security assessments."
Manish Talwar
CEO, Goalstox
"As miniOrange's technical co-founder, Sushma crafted a scalable, secure, and sustainable technical architecture for the initial IDP product, often burning the midnight oil. Her hands-on demos, even under tight timelines, consistently delighted our customers."
Anirban Mukherji
CEO, miniOrange




