CYBER ASSESS
Cyber Assessment as a Service
Understanding & Managing Your Cyber Risks
At BUZZ, we recognize the complexities of the digital realm. Our Cyber Assessment as a Service (CAaaS) offers a comprehensive, custom and proactive dive into your entire digital infrastructure.
We take ownership, collaborating closely with your team to ensure your business remains secure, compliant, and ahead of potential threats.
CORE OFFERINGS

Vulnerability Assessment
It pinpoints & measures security vulnerabilities across networks, systems, applications, offering insights into potential threats.
Penetration Testing
Penetration Testing, often known as “ethical hacking,” is a simulated cyber attack on your system to evaluate its security.

Risk Assessment
Risk Assessment is a strategic process that evaluates potential threats and vulnerabilities relevant to your business operations.

Security Audit
A Security Audit is a systematic evaluation of the security of an organization’s information system against a set of established criteria.

Vulnerability Assessment
Vulnerability Assessment is a process that pinpoints and measures security vulnerabilities across networks, systems, applications, offering insights into potential threats. At BUZZ, our tailored approach ensures that each assessment is uniquely aligned with your business environment. We combine our team’s expertise with advanced tools, delivering clear and actionable insights to strengthen your security.
What We Do
- Tailored Scans: We conduct scans specific to your business, covering internal, external, and cloud environments.
- Continuous Monitoring: Our assessments are ongoing, ensuring timely identification and management of new vulnerabilities.
- Clear Reporting: We provide concise reports, focusing on meaningful insights rather than overwhelming data.
- Custom Solutions: We adapt our assessments based on your specific operational needs.
- Expert Guidance: Our team offers in-depth analysis and recommendations, guiding you every step of the way.
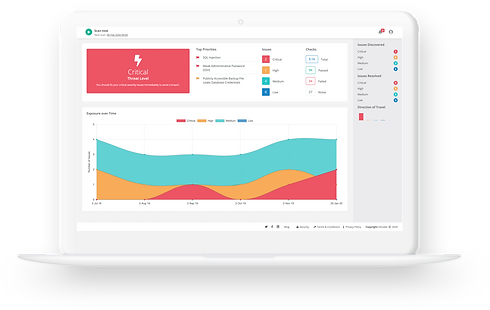

Penetration Testing
Penetration Testing, often known as “ethical hacking,” is a simulated cyber attack on your system to evaluate its security. It’s about testing your defenses by mimicking the actions of potential attackers. At BUZZ, we go beyond standard testing methodologies. Our experts, equipped with the latest tools and techniques, dive deep to uncover vulnerabilities that might be overlooked in traditional tests.
What We Do
- Real-World Scenarios: We simulate genuine cyber attack scenarios to provide a comprehensive view of potential threats.
- Diverse Expertise: Our team has expertise in various domains, including Web, Mobile, APIs, and IoT.
- Collaborative Approach: With our Pentest-as-a-Service, we offer a real-time dashboard for easy collaboration and instant feedback.
- Detailed Reporting: We provide comprehensive reports detailing vulnerabilities, risks, and recommended mitigation strategies.
- Continuous Engagement: Our engagement doesn’t end with a report. We work with you to ensure vulnerabilities are addressed and your systems are secure.

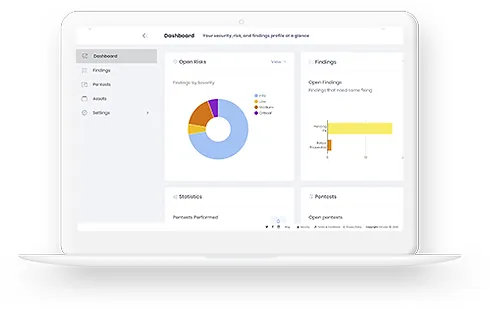
Risk Assessment
Risk Assessment is a strategic process that evaluates potential threats and vulnerabilities relevant to your business operations. It’s about understanding the risks that could impact your assets, data, and reputation. At BUZZ, we take a holistic approach to risk assessment. Utilizing industry-standard frameworks, like NIST, combined with our expertise, we provide a comprehensive view of your organization’s cyber risk landscape.
What We Do
- Framework-Based Evaluation: We use the NIST framework for a thorough threat assessment, ensuring alignment with industry best practices.
- Risk Prioritization: Using a risk matrix, we prioritize threats, helping you focus on the most critical vulnerabilities first.
- Actionable Insights: Our assessments result in a 5-Point Maturity Model, offering clear steps to enhance your security posture.
- Executive-Level Reporting: We tailor our reports for executive understanding, highlighting top-prioritized risks.
- Partnership and Commitment: At BUZZ, we go beyond mere risk identification, partnering with you to ensure a resilient and empowered future.
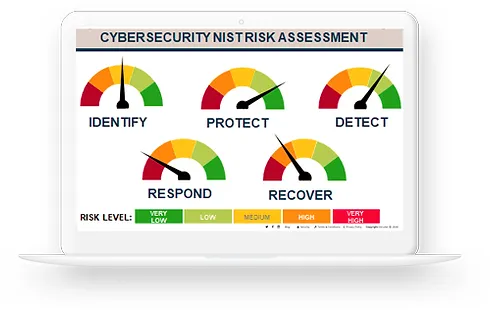

Security Audit

A Security Audit is a systematic evaluation of the security of an organization’s information system. This audit assesses how well the organization’s current security measures are performing against a set of established criteria. At BUZZ, we believe that a thorough security audit is foundational to understanding and strengthening an organization’s cybersecurity posture.
What We Do
- Comprehensive Review: We meticulously examine your policies, procedures, technical systems, and physical security controls to identify any areas of concern.
- Gap Analysis: By comparing your current security measures against industry best practices and standards, we identify gaps and provide recommendations for improvement.
- Actionable Recommendations: Our audit results in a detailed report, providing clear and actionable steps to address any identified shortcomings.
- Stakeholder Communication: We ensure that all relevant stakeholders, from technical teams to executives, understand the audit findings and their implications.
- Ongoing Partnership: At BUZZ, our relationship doesn’t end with the audit. We remain committed, assisting you in implementing recommendations and ensuring continuous security improvement.
Trusted by companies of all sizes





Please leave your details.
We’ll BUZZ you!
THAT’S NOT ALL
Learn more about other Services
Credits earned by the Founder & BUZZ
"BUZZ swiftly identified key vulnerabilities in our security, implementing access control and architectural changes.Their hands-on approach made them an extension of our team, not just a vendor, enhancing our overall success."
Mahendra Pratap
CEO, Asti Solutions
"Our partnership with BUZZ for a penetration test was impressive. Their speed, thoroughness, and professionalism identified critical vulnerabilities, making them a top recommendation for comprehensive security assessments."
Manish Talwar
CEO, Goalstox
"As miniOrange's technical co-founder, Sushma crafted a scalable, secure, and sustainable technical architecture for the initial IDP product, often burning the midnight oil. Her hands-on demos, even under tight timelines, consistently delighted our customers."
Anirban Mukherji
CEO, miniOrange




